Table of Contents
Definition
The Secure Socket Tunnelling Protocol (SSTP) is a common protocol used in Virtual Private Network (VPN) connections. The protocol was developed by Microsoft, so it’s more common in a Windows environment than Linux. Microsoft developed the technology to replace the more insecure PPTP or L2TP/IPSec options available in Windows. Native VPN connections in Windows mostly use SSTP, but the VPN provider and the ease of setup for users and administrators dictate the protocol.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we’ll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
What Is SSTP Used for & How Does It Work?
Any VPN connection requires a client and a server. Both the client and server must “agree” on the protocol and support the connection. Traditional Point-to-Point Tunnelling Protocol (PPTP) connections do not use SSL/TLS, so SSTP was introduced to improve the security of data transfers and to avoid limitations set up by firewalls that block specific ports. Unlike PPTP, SSTP uses SSL/TLS, secure key negotiations, and encrypted transfers.
SSTP is used for secure connections, and the technology behind it leverages SSL/TLS handshakes. It uses the same port as SSL/TLS (port 443), and it bases the connection on user authentication instead of a device. It’s popular with internet connections that must have improved security over basic SSL/TLS connections. It’s often compared to the OpenVPN standard, which is considered the gold standard in encryption libraries.
How Secure Is the SSTP Protocol?
Windows Vista introduced the SSTP standard, and it persists as a trusted secure protocol in Windows 7, 8, and 10. If you use the Windows operating system, its native libraries make it convenient to use and secure against eavesdropping and other side-attacks. It’s a chosen resource by many organisations that rely on encrypted communication between two locations.
While SSL/TLS is a part of the SSTP protocol suite, you still must consider the cryptographic library and version used to encrypt data. SSTP uses the AES (Advanced Encryption Standard) encryption cipher, making it a safe option. It uses 256-bit encryption with the AES encryption cipher, which is currently considered cryptographically secure. Even though AES-256 encryption can be slow, SSTP is still considered a fast protocol for tunnelled and encrypted communications.
How to Connect to SSTP VPN
When you sign up for a VPN service or have it at your workplace, you might be able to use Windows SSTP. Your provider or system administrator can let you know if SSTP is an option for you. To configure SSTP VPN in Windows 10, follow these general steps.
- First, go to your network settings.
- Type “Network and Internet” in the search bar or open the settings from the Windows Control Panel.
- Click “Network and Internet” when you see the control panel list of options.
- You’ll see the following configuration screen:
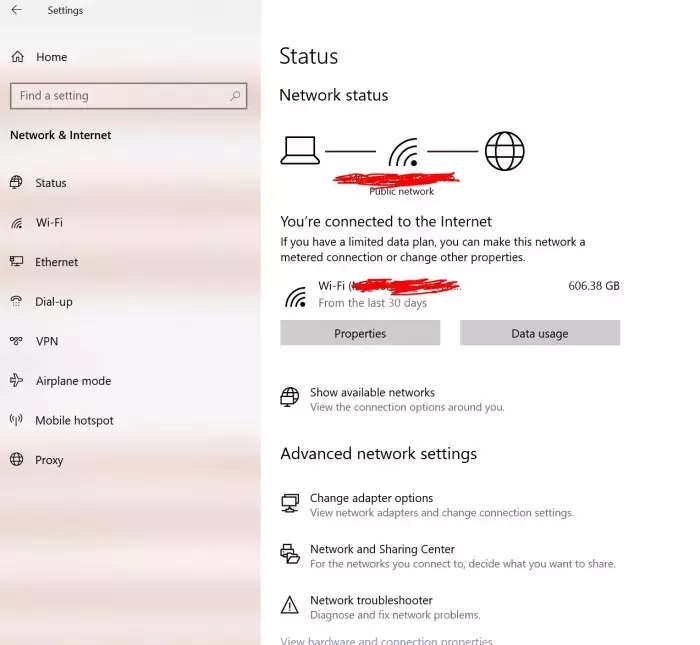
- Click the VPN option on the left panel, and you see this configuration window:
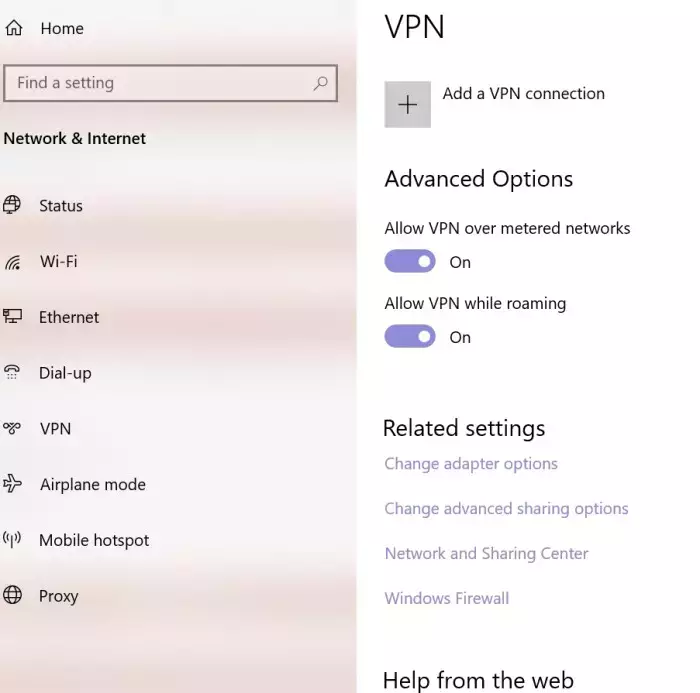
- Click “Add a VPN connection” at the top of the window. You are then shown a screen where you configure the VPN connection. Note that the connection settings depend on your service provider or workplace setup.
- The window looks like the following:
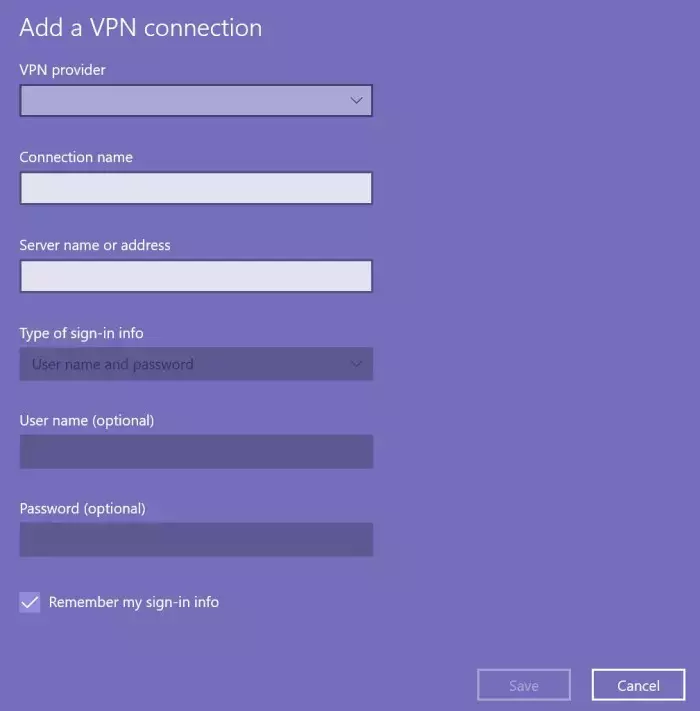
- Make sure the “Remember my sign-in info” checkbox is checked, or every time your computer reboots, you’ll need to reconfigure the VPN settings.
- After you save these settings, you now have a VPN configured on your Windows desktop, which can be used every time you connect to a sensitive server.
Any time you use public Wi-Fi, you should turn on your VPN. SSL/TLS encryption alone doesn’t automatically mean an attacker can hijack your connection and eavesdrop on data. A VPN adds protection to your connection by packaging your data and “tunnelling” it from your computer to the server. If an attacker eavesdropped on your data, they still could not brute force encrypted data despite the server’s outdated and cryptographically insecure SSL/TLS version.
SSTP vs. PPTP
The point-to-point protocol (PPTP) is older and used by older VPN providers, but the newer SSTP option has several advantages and disadvantages. PPTP is still secure and easier to set up. Since it’s an older protocol, it’s more reliable and stable than a newer protocol such as SSTP.
The main benefit of PPTP is that it’s widely supported. If you need to choose from a wide range of VPN providers, any device that supports PPTP will have no issues connecting to the selected VPN servers. Because it’s an older protocol, PPTP developers have had plenty of time to optimise it and find ways to make it efficient, so it’s good for speed.
The most significant disadvantage of PPTP is that internet service providers or workplace administrators can block it. SSTP, however, uses port 443, which is the SSL/TLS port used in web applications. Since SSTP uses the same 443 port, it isn’t typically blocked on any network, including a workplace environment. You can use an SSTP VPN on any network without worry about administrators restricting it.
The main disadvantage for users who prefer SSTP is that Microsoft owns it and, therefore, has little transparency. It’s easily integrated into any current version of the Windows operating system, but this benefit only works for Windows devices. Linux users don't have this benefit and usually prefer PPTP if they only have a choice between SSTP and PPTP.
SSTP vs. OpenVPN
Of the three protocols – SSTP, OpenVPN, and PPTP – OpenVPN is the newest. It uses the OpenSSL library, which is common in a Linux environment. OpenSSL is an open-source library responsible for the Heartbleed security vulnerability. Still, contributor code updates and reviews make OpenVPN and its OpenSSL library one of the most secure choices on the market today.
OpenVPN uses an AES encryption cipher, which is considered the gold standard in symmetric key encryption. It’s much more reliable than the other two options, and most providers support it. The only disadvantage with this protocol is that it takes more technical experience to set up the environment. It also bypasses firewall restrictions, just like SSTP.
Compared to SSTP, OpenVPN is more widely used and accepted, but it might be too technical to set up for users unfamiliar with its settings. Since SSTP is easy to set up and integrates easily with Windows, it’s often the choice in Microsoft environments over OpenVPN.